A group of researchers in the US discovered three new vulnerabilities in 4G and 5G technologies that could allow an attacker to intercept a phone call and track the location of a mobile phone user. The discovery is said to be the first vulnerability to affect both the 4G and 5G standards. The researchers also said that the new attack methods they developed can beat new protection measures. Syed Rafiul Hussain, a co-author of the report, said: “Anyone who knows a little cellular paging protocol can launch this kind of attack.”
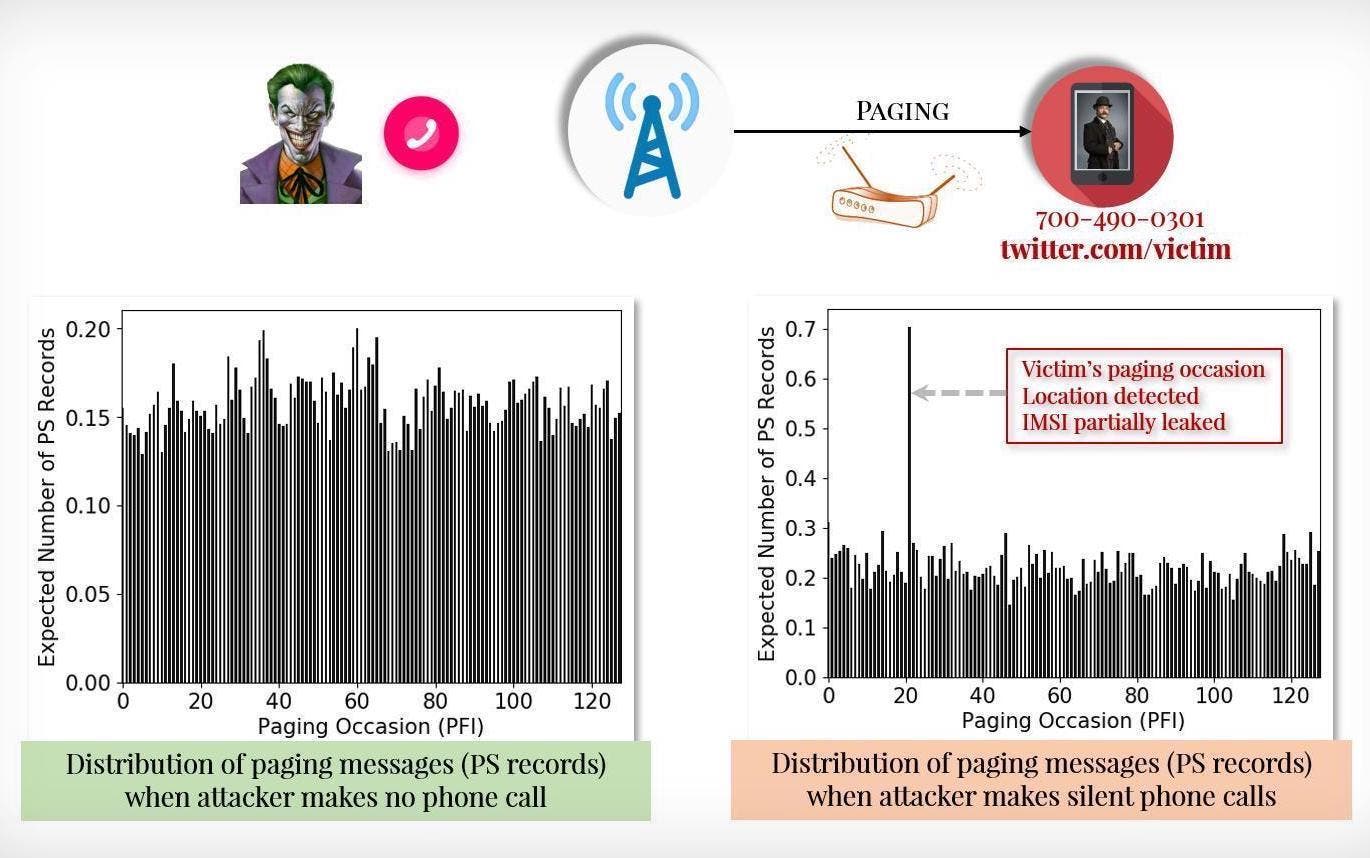
The report elaborates on the attack process: They first use Torpedo (Paging Message Distribution) to exploit the vulnerabilities in the paging protocol, which operators use to notify mobile phones before text messages and phone calls. These researchers found that by making a few phone calls and cancellations in a short period of time, a page message can be sent without notifying the target device that there is a phone call, and the attacker can use this lapse to track the victim’s location.
After understanding the victim’s paging period, the attacker can hijack the paging channel and inject or reject the paging message by sniffing the Aberdeen alert or other information or completely blocking the information. Torpedo opened the door for two other attacks: one is Piercer, the researchers said it allows the attacker to determine the IMSI (International Mobile Subscriber Identity) on the 4G network; the other is the so-called IMSI crack attack, which can be used in 5G and can violently crack the encrypted IMSI identifier on the 5G network.
As a result, even the latest 5G devices are likely to face the threat of stingray – law enforcement officers use this technology to determine someone’s real-time location and record all the phones in their area. Hussein also said that some of the more advanced devices can also intercept calls and text messages. They said that the four major US carriers will be affected by Torpedo, and the radio equipment needed to launch an attack will cost as little as $200. One company’s network was also affected by the Piercer attack, but the researchers did not disclose the specific identity. As of now, none of the top four US carriers commented on this.





