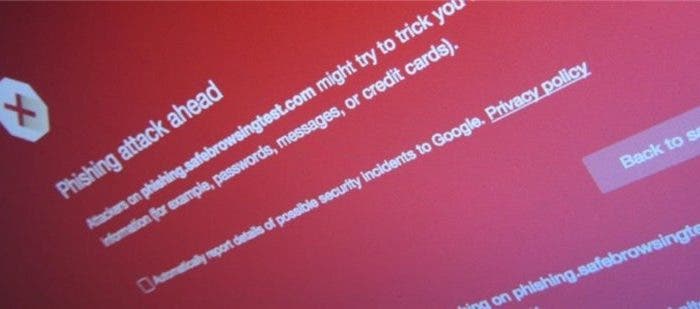
According to ZDNet, a research team consisting of Arizona State University scholars and PayPal employees recently announced that due to problems with Google’s Safe Browsing API, mobile browsers such as Chrome, Firefox, and Safari to fail to display phishing attack warnings for about 18 months.
The researchers said: “We identified a gaping hole in the protection of top mobile web browsers,” the research team said. “Shockingly, mobile Chrome, Safari, and Firefox failed to show any blacklist warnings between mid-2017 and late 2018 despite the presence of security settings that implied blacklist protection.” However, this issue only affects mobile browsers that use Google Safe Browsing Link Blacklist technology.
The research team has notified Google of the problem, which was fixed at the end of 2018. The researchers said: “After we disclosed this vulnerability, we learned that the inconsistency in the mobile GSB blacklist was due to a transition to a new mobile API designed to optimize data usage, which ultimately did not work as expected.”
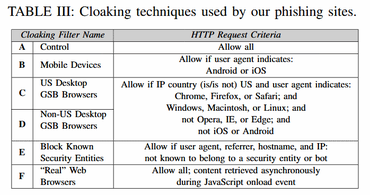
This major security breach was discovered in an academic research project called PhishFarm, which was launched in early 2017. During this time, the researchers created and deployed 2,380 phishing pages that mimicked PayPal logins, but instead of measuring the speed at which URLs appeared on the URL blacklist, they focused on deploying phishing pages with “disguise technology.” The purpose of these pages is to trick URL blacklisting techniques and then record the time it takes for these “disguised” phishing pages to enter the “dangerous sites” list.
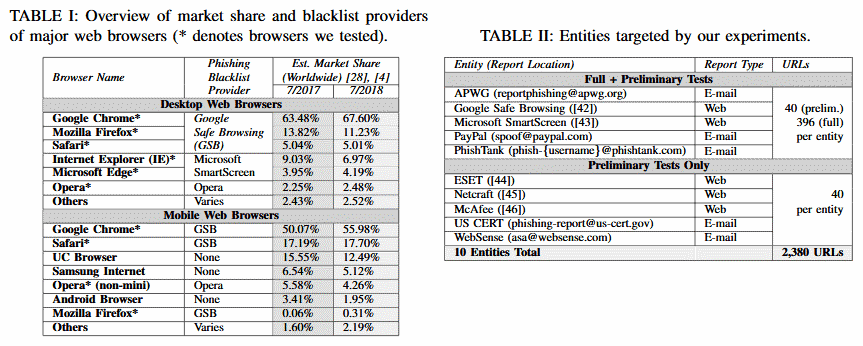
For PhishFarm, the researchers tested a number of URL blacklists, such as Google Safe Browsing, Microsoft Smart Screen, and blacklists managed by US-CERT, Anti-Phishing Working Group, PayPal, PhishTank, Netcraft, WebSense, McAfee, and ESET. In addition, the research team’s phishing page uses six camouflage techniques, and researchers say they have seen the use of these phishing tools in the real world.
The researchers said: “We found that simple camouflage techniques that represent real-world attacks – including attacks based on geography, device type or JavaScript – can effectively reduce the likelihood of blacklisting by more than 55%. Blacklists and camouflage techniques have different detection results, but the most striking thing is that many phishing attacks have not been detected on mobile browsers that use Google Safe Browsing URL blacklists.”
When the researchers repeated their tests in mid-2018, they got the same results, when they realized that Google’s Safe Browsing technology was not as secure on the mobile device as expected. However, the researchers said that the problem was finally resolved by the end of 2018.