Google researchers have confirmed in recent hours that in 2017 criminals were able to pre-install an advanced backdoor on Android devices before they left the factories of their respective manufacturers.
We are talking about Triada, a Trojan discovered in 2016 by Kaspersky Lab and which we also dealt with in 2017, when a list of infected devices was published thanks to the work of Dr. Web researchers.
Well, the Google team confirmed Dr. Web’s report, even though it didn’t name the devices affected by the problem, explaining that the attack was launched by one or more partners used by the manufacturers to prepare the final firmware image to install on the devices in question.
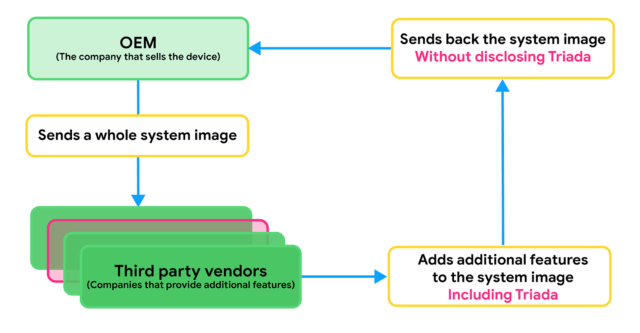
According to Lukasz Siewierski, a member of Google’s Android security and privacy team, Triada infects device system images through a third party during the production process (sometimes manufacturers include features that are not part of the open project Android source, such as unlocking with the face and therefore collaborating with third parties to add the desired features).
According to what has emerged, the supplier responsible for infecting the image of the system with Triada uses the name Yehuo or Blazefire.
According to Siewierski, “The Triada case is a good example of how Android malware writers are becoming more skilled” and confirms that Google’s decision to collaborate with various manufacturers to prevent such problems is the way to go.





