American manufacturing giant, Google, recently announced that it has raised the reward for Chrome security vulnerabilities up to $30,000. In 2010, Google launched the Chrome Vulnerability Reward Program. So far, this program has gotten over 8,500 valuable reports. Its total bonuses total more than $5 million.
Participating in this reward program are Windows 7/8.1/10, macOS 10.10+, Linux, Android 4.4+, Chrome on iOS 7+, and the latest version of Chrome OS. You can win prizes by finding valuable security breaches in these systems.
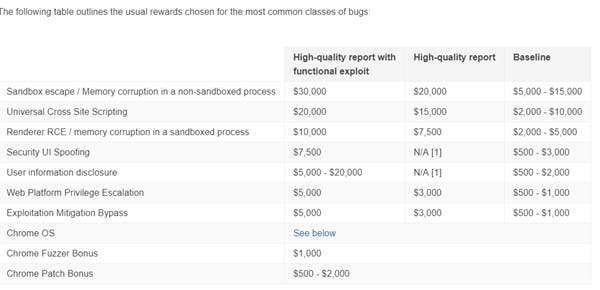
The most valuable is the sandbox escape and non-sandbox thread memory exception. Find the relevant vulnerabilities to get at least $5,000 – $15,000. According to Google, high-quality findings can get $20,000. If you can give an executable exploit code, you will get $30,000. Others include general cross-site scripting, renderer RCE, sandbox process memory anomalies, security interface induction, user information disclosure, Web platform privilege escalation, etc. These all attract at least $500, up to $20,000.
At the 19th Privacy Enhancement Technology Symposium in Stockholm, Sweden, Boston University researchers announced a new vulnerability in the Bluetooth Low Energy (BLE) communication protocol. This causes a large number of devices to leak user identity information. Apple and Microsoft systems are not safe but Android is. The study shows that Windows 10, iOS, macOS and even Apple Watch, Fitbit and other devices have this vulnerability. They will periodically send advertising events containing custom data structures for interaction with other devices and platforms. According to the researchers, Android devices are safe. This is because Google’s system doesn’t send messages and exposes itself, but scans nearby broadcasts.





