Android is the target of a new banking malware called Ginp. According to ThreatFabric experts, the virus reuses Anubis malware code to steal the bank account of its victims without their knowledge.
Spotted by Kaspersky at the end of October 2019, the Ginp malware has been hovering on Android devices since June 2019, reports ThreatFabric, a computer security firm, in a new report. According to the researchers, the malware is still in development. The hackers rely mainly on the code of Anubis, a dangerous malware capable of looting the bank account and Paypal of its victims.
Android: A malware disguised as Adobe Flash Player
Since June, 5 versions of the malware have been identified on the web. The malware masquerades as popular applications, such as Adobe Flash Player, or for a fictional application called Google Play Verificator. For the moment, it is spreading only through APK files available on the web. Ginp, is clearly not yet able to penetrate the Google Play Store.
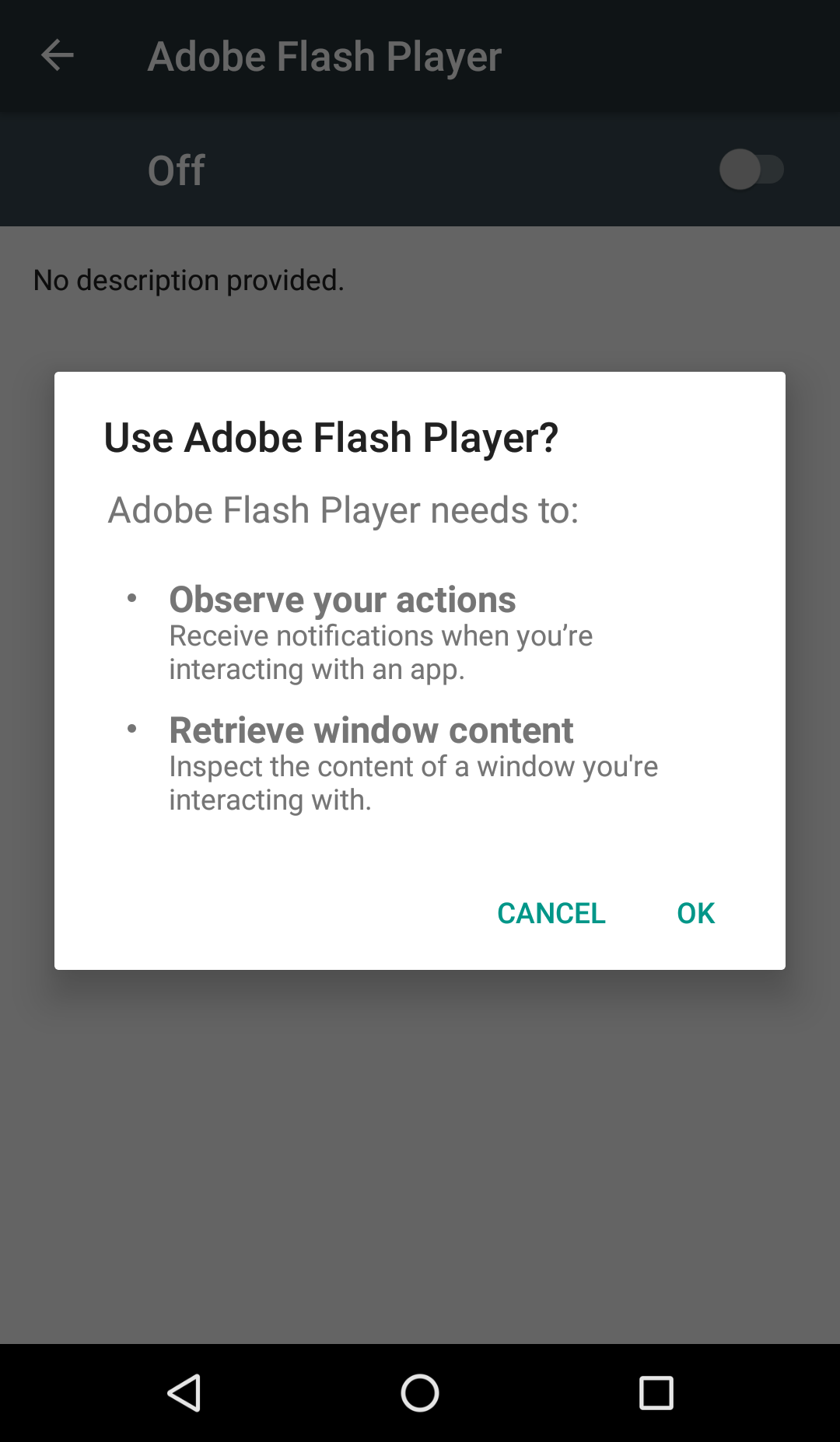
Once infiltrated on your smartphone, Ginp will start by removing the icon of the fraudulent application installed from the application drawer. This way, users are not likely to delete the application if they notice something wrong. Many malware, including the invincible trojan xHelper, proceed in this way. In a second step, the malware will request access to the accessibility services of the smartphone. As a reminder, these services offer privileged access to certain features of Android to facilitate the use of people with disabilities.
Ginp will then be able to collect and send SMS, make calls without your knowledge, and launch malicious commands. The malicious software will display dummy windows when you open the application of your bank. Ginp is able to perfectly imitate the interface of the application to recover your bank details. In the process, the malware also asks for the details of your credit card. This information is then used to steal your account or resold it in the dark web markets.
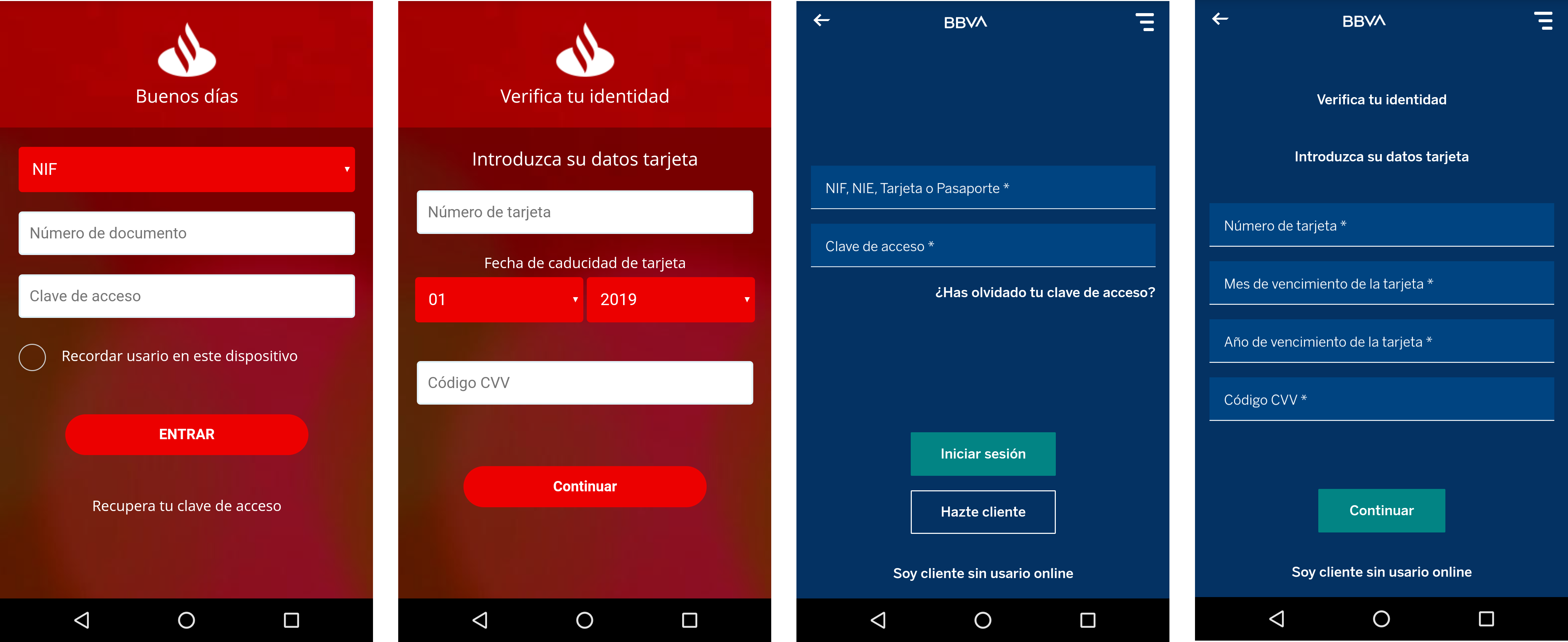
According to ThreatFabric, Ginp also asks for your credit card details when making a purchase on the Google Play Store. So users can communicate their data to hackers without any suspicions. For the time being, the malware targets mainly Spanish banking applications. Including Caixa, Bankinter, Bankia, BBVA, EVO Banco, Kutxabank and Santander. According to the report, Ginp could spread to the rest of Europe. For security, we invite you not to install any APK file and to stick to the applications offered on the Google Play Store or on trusted sites.






This was only a matter of time with the discontinuation of flash. Flash will not disappear, even with google and firefox removing support. I myself have flash-capable versions of firefox stashed away and I use the Puffin Flash Browser for android.
Until such a time where there is a suitable replacement for actionscript (No, html5 isn’t) in flash games and animations it’ll be here. I’d say people will still be using it 10 years from now, I know I will.