
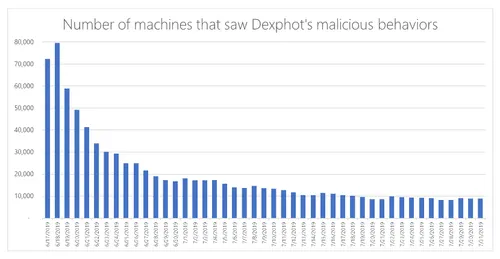
Today, Microsoft detailed that a new malware strain has been infecting Windows computers via Dexphot since October 2018. Its peak was in June when the number of infected computers was over 80.000.
Dexphot is a complicated malware, which is a tool for hackers to mine cryptocurrencies and generates revenue for the attackers. Thus, it doesn’t steal user data.
This malware started from harming the content of two legitimate processes - svchost.exe and nslookup.exe. Then, they used tasks to make the victim be infected once every 90 minutes. Further, they effectively used polymorphism, which makes all systems very complicated.
Among all tasks, the most eye-catching thing is “polymorphism camouflage”, which is able to change footprint and file names on the computer every 20-30 minutes. Thus, it makes Windows computers more vulnerable in terms of cybercriminal aspects.
Dexphot is equipped with 5 files: an installer with 2 URLs, a loader DRL, and an encrypted data file, which includes 3 additional files. Since all processes are legitimate, except for the installation process, recovery is very difficult. Moreover, Dexphot used to deal with computers that were previously infected by other malware, i.e it makes the problem more complex.
It is predicted that Dexphot will be able to harm some other important processes such as svchost.exe, tracert.exe, and setup.exe. Furthermore, it would also employ a technique called "living off the land" to abuse legitimate Windows processes and to execute malicious code, rather than run its own processes. According to Microsoft, Dexphot was able to use unzip.exe, powershel.exe and so on for its ‘purposes’.
Although Dexphot has strong persistence mechanisms, no malware stays unrevealed forever. And due to efforts and relevant policies of Microsoft, the number of attacks is continuously declining.
Popular News
Latest News
Loading




