Mac security researcher Patrick Wardle said that he found the most likely first malicious program in history to lock the Apple M1 device. It is GoSearch22, a legitimate extension of Safari, and a variant of the Mac malicious adware Pirrit. Wardle believes that M1 users have been infected, and the ability of antivirus software to detect it needs to be strengthened.
The M1 is an Apple-made chip that has been applied to Apple devices such as MacBook Air, 13-inch MacBook Pro and Mac mini. Because it adopts the Arm architecture, Apple encourages developers to create native programs based on this architecture. Apple also provides Rosetta 2 on macOS to translate Intel-based applications into Arm architecture so that Intel-based programs can also run on the Apple M1.
Also Read: Apple M1 Breaks AnTuTu Benchmark Crossing The 1 Million Points Barrier
Wardle explained that the Arm-based applications on the Apple M1 are significantly better than those converted through Rosetta 2. He also started to change the various open source tools of Objective-See to the Arm architecture. He also thought that Malware authors would not have the same idea. So they decided to check out VirusTotal website, which collects a large number of virus samples.
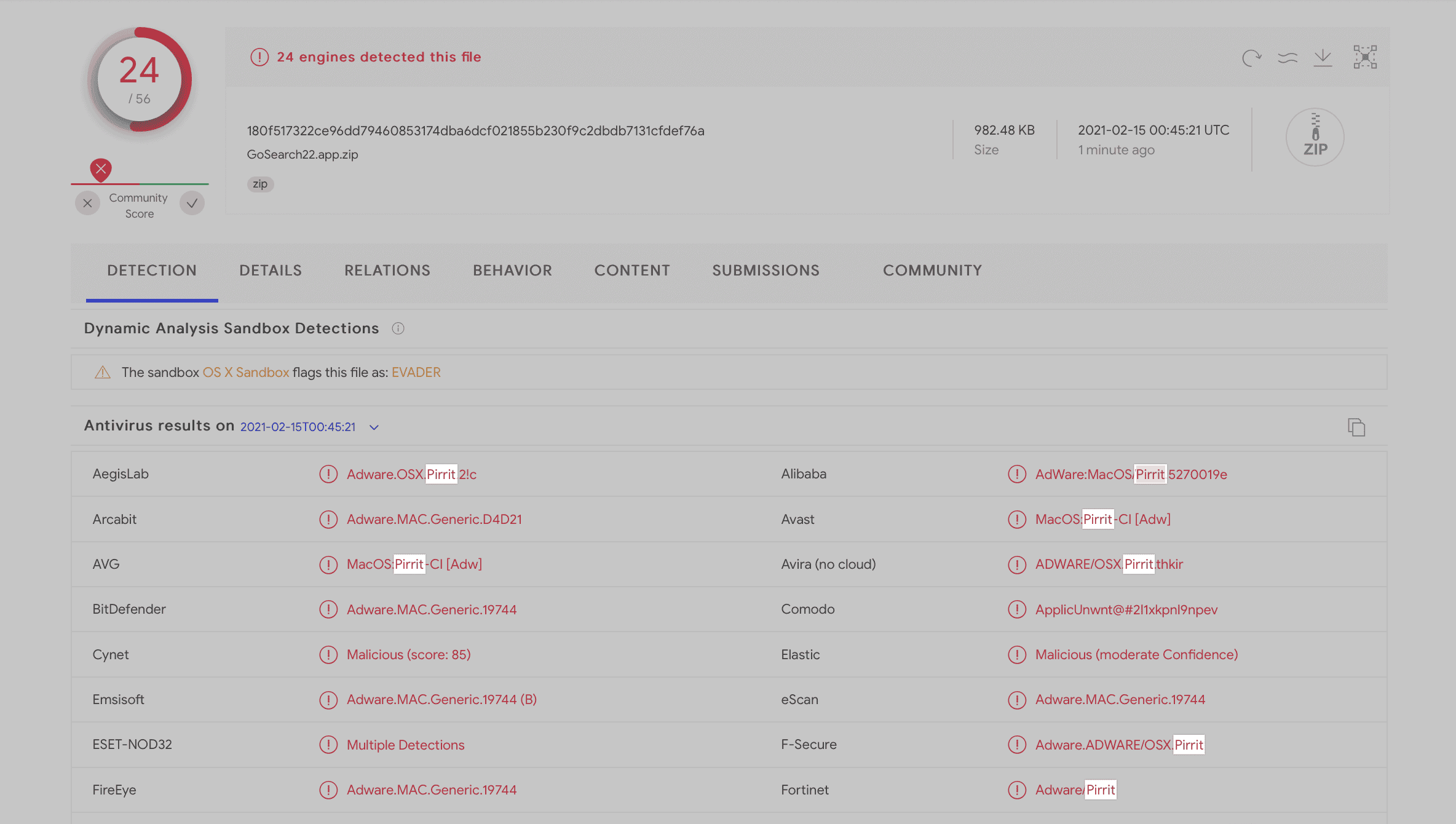
Wardle filtered the virus samples uploaded to VirusTotal by various researchers and found GoSearch22. The latter is a variant of the malicious adware Pirrit. But it is a native Apple M1 program that can be executed on M1 devices without conversion. Its author also has an Apple developer ID. Since GoSearch22 is uploaded to VirusTotal by the user, Wardle believes that the M1 users have been infected.
GoSearch22 And Its Author
GoSearch22 is an extension of Apple’s Safari browser. When the M1 users install the extension, they will see coupons, banner ads, surveys, or other types of advertisements that pop up from time to time, and they usually do so. The ad program also collects user browsing information, including IP address, visited web pages, search string entered or user location.
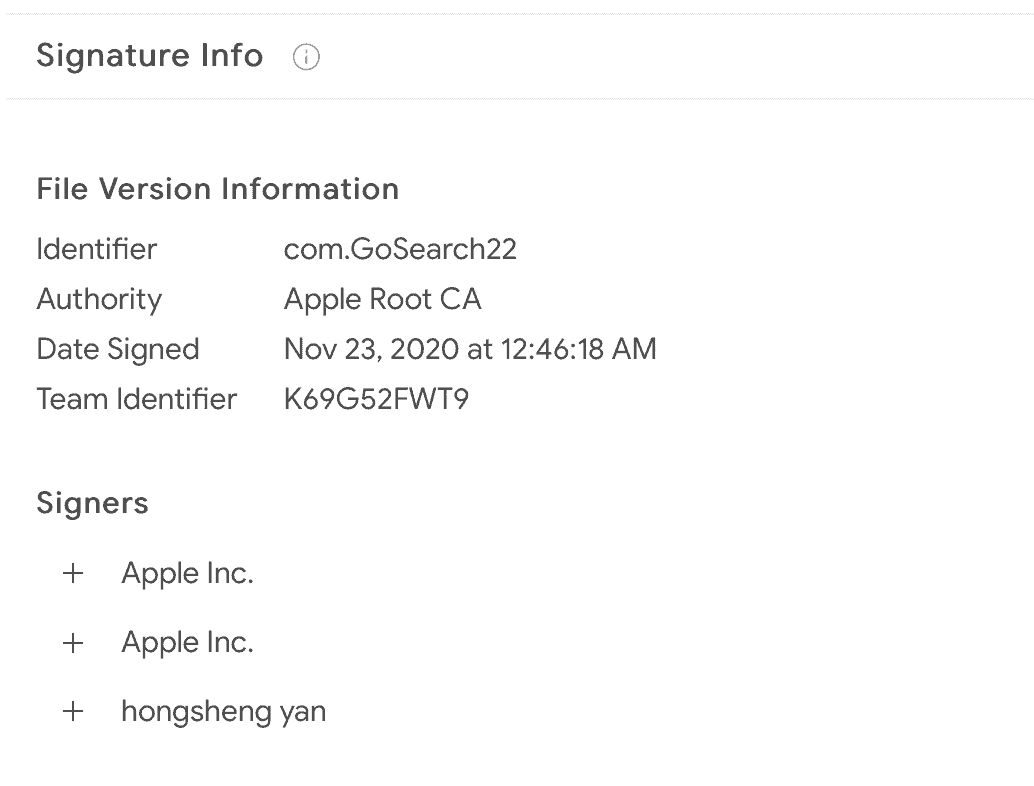
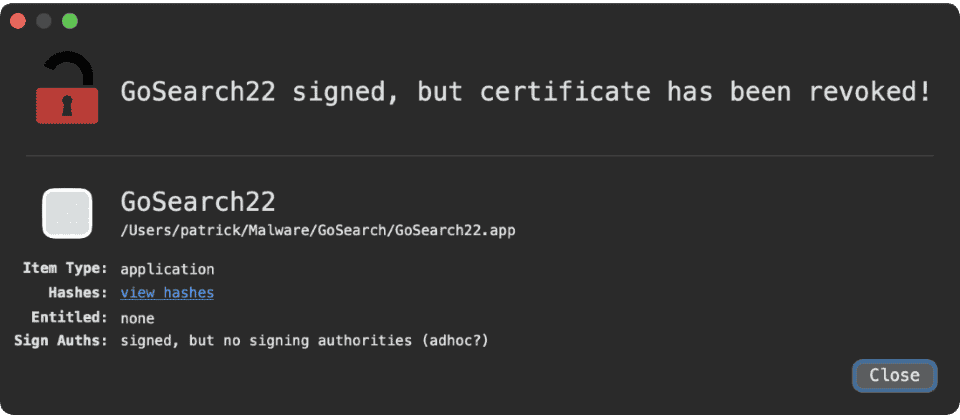
GoSearch22 was signed by Apple developer hongsheng yan on November 23 last year. It was uploaded to VirusTotal at the end of December last year. When Wardle announced this research on February 14, Apple has also withdrawn GoSearch22 certificate.
Wardle believes that the appearance of GoSearch22 means that malware authors are also improving their programs with the times to meet the latest hardware and software environments on the market.





