Recently, cybersecurity experts from Cleafy said that there had been a spike in Android remote access trojan (RAT) infections over the past year. This dangerous malware campaign had been spreading to a number of regions. Its name is BRATA, and this malware was first discovered in Brazil. But now, it appeared in Italy as well. Well, as for its activity, hackers are using this malware to steal banking details from Android users. Of course, later, they withdraw money from those accounts.
What makes this malware more dangerous is that the BRATA is difficult to detect.
Also Read: Android Malware Is About 47 Times That Of iOS – Tim Cook
This is how BRATA works. First, users get an SMS text message that contains a link to a website. Users think the text comes from the bank. (As you know, it’s called smishing (phishing with SMS)). Once users click the link, they will appear on a site that suggests downloading an anti-spam app. To make it more trustworthy, it also says that a bank employee will contact them soon to discuss the details of the app.
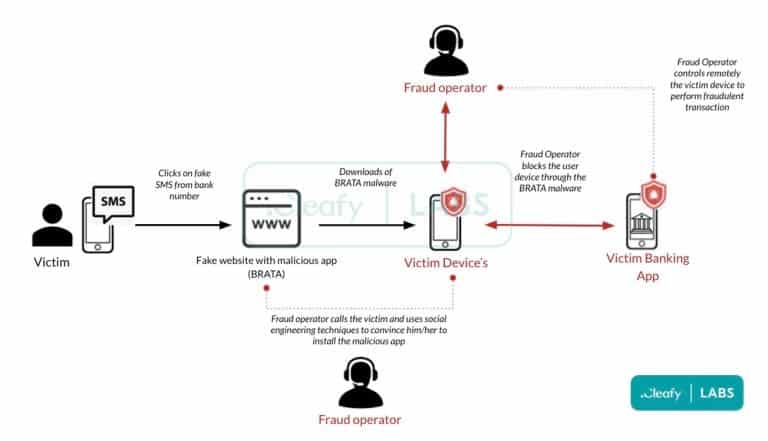
Apart from this, on the opened webpage, you should fill the fields with your bank information. This is to prove you have an account. Then, a real person will attempt to sway you into downloading the malicious app. For this, they are using various social engineering techniques. Those who believe in this will install the app that is used by hackers to control your phone.
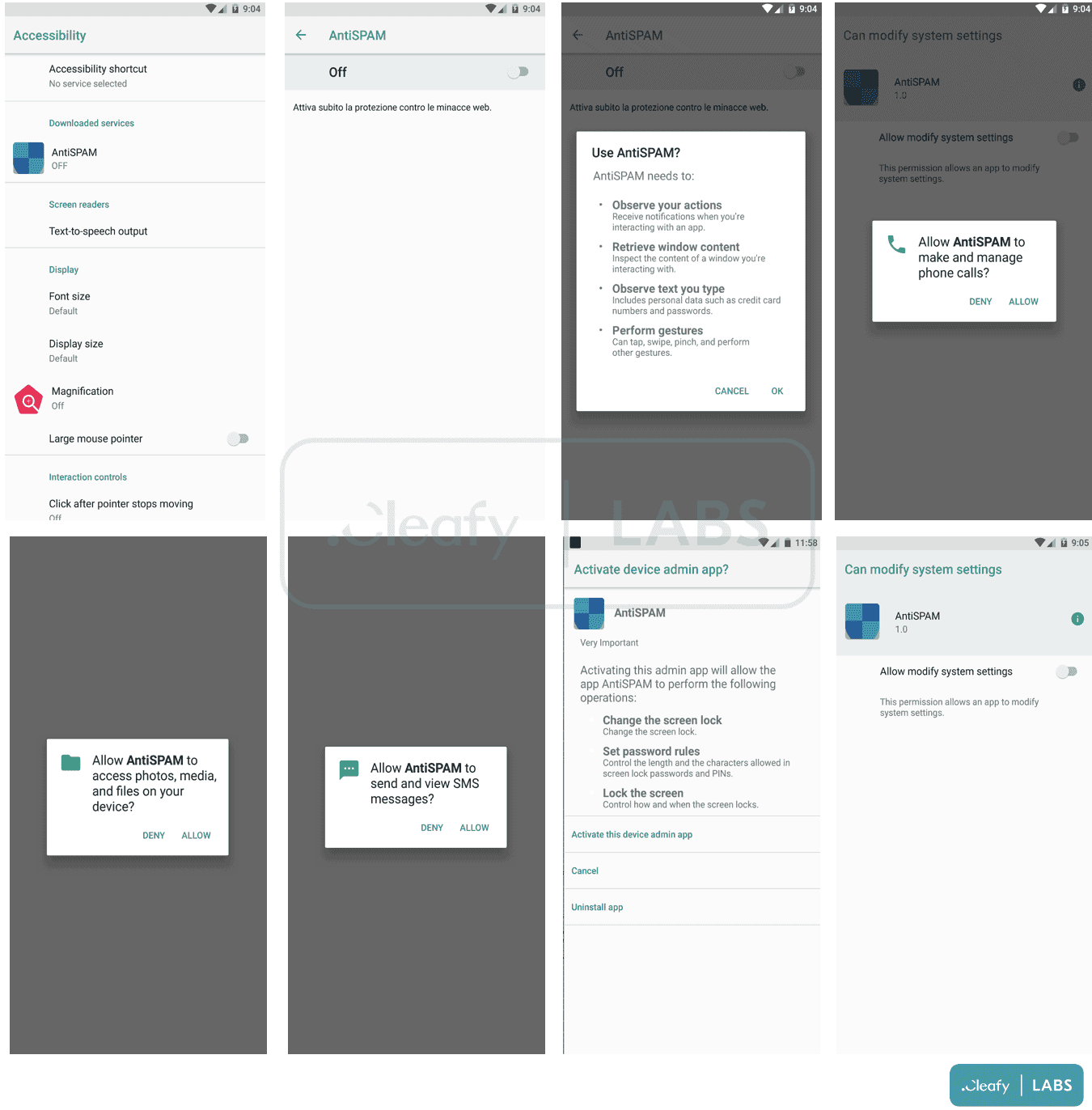
How Does the BRATA Malware Work?
- First, it intercepts SMS messages and forwards them to a C2 server. The hackers use this technique to get 2FA sent by the bank via SMS during the login phase or to confirm money transactions.
- Second, they use various screen recording and casting features to collect any sensitive information displayed on the screen. Say, it includes audio, passwords, payment information, photo, and messages. You may wonder how it works if the user doesn’t click the record button. But the thing is via the Accessibility Service, the malware clicks the “start now” button itself. So it doesn’t wait for users to click on it.
- Third, it realizes self-destruction from the device to reduce detection.
- It will even uninstall antimalware or antivirus applications.
- Of course, it will hide its icon app not to be visible to users.
- The BRATA malware will disable Google Play Protect in order to avoid being flagged by Google as malware.
- It will give more privileges to itself modifying the device settings.
- More interestingly, the malware is capable of unlocking the device if there is a secret pin or pattern.
- Lastly, it will send the collected information to the special server.