Beware of this new Vidar malware distribution campaign. The malware now hides in files with the extension .CHM. These are Microsoft Help files found in most Windows applications and services.
Trustwave security experts are sounding the alarm: a new wave of distribution of Vidar, a well-known and particularly pernicious malware, is underway. But rather than hiding in an executable, the malware hides this time in a Microsoft help file.
The malware spreads via classic spam that you receive in your mailbox. The message contains an attachment, which the sender encourages you to open with these words: “This important information is for you. Please see the attachment to this email”. And that’s where the malware comes into play.
To hide itself even better from the eyes of its victims, the malware hides in a .DOC file named “REQUEST.DOC”. But don’t be fooled by its extension, it’s actually an .ISO file. Inside, there is an HTML file compiled in CHM format, generally called “PSS10R.CHM”. And still within the ISO is an executable named “APP.EXE”.
Dangerous Windows Malware Hiding in Microsoft Help Files
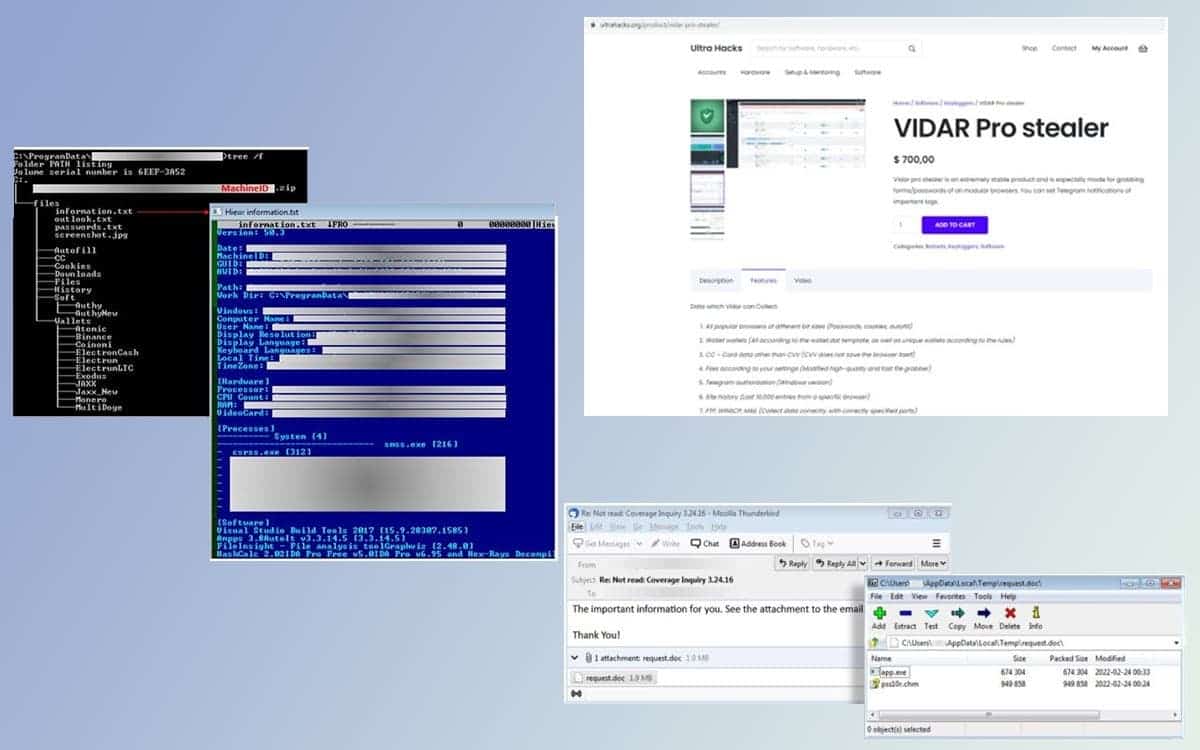
Once the CHM file or executable is open, a small JavaScript code launches. The Vidar malware can then commit its misdeeds. It creates its own folder in C:\ProgramData and sends the collected data to a server. If necessary, it is also able to download another executable, also a malware. Once committed, the malware erases its own traces in the ProgramData folder and deletes the DLLs created for the occasion.
Vidar is capable of recovering operating system data, but also and above all user data. He can also steal all payment data (credit card, online payment service, etc.). And to close it all, it is even possible for him to steal the information allowing him to identify himself to a cryptocurrency service.
The first appearance of the Vidar malware dates back to 2018. The software is from a Russian origin. Why such an assumption from the security experts who discovered Vidar? The malware immediately stops its abuses when it is installed on a machine located in Russia, or the keyboard of the infected PC has a Russian keyboard.
As usual, we advise you never to open an attachment from an unknown sender. Secondly, scan this attachment using an antivirus, such as BitDefender, Norton Security, Avast or Microsoft Defender.





