Hackers are using malicious shopping apps that aim at stealing the bank details of users in Malaysia and could target other countries soon. These threat actors specifically target customers of eight banks in the country. As part of their strategy, hackers develop legitimate-looking websites that are actually fraudulent. Moreover, these websites are designed to convince users to download the apps. The Slovak cybersecurity firm ESET shared this piece of information in its report. These dummy websites bear a striking resemblance to cleaning services.
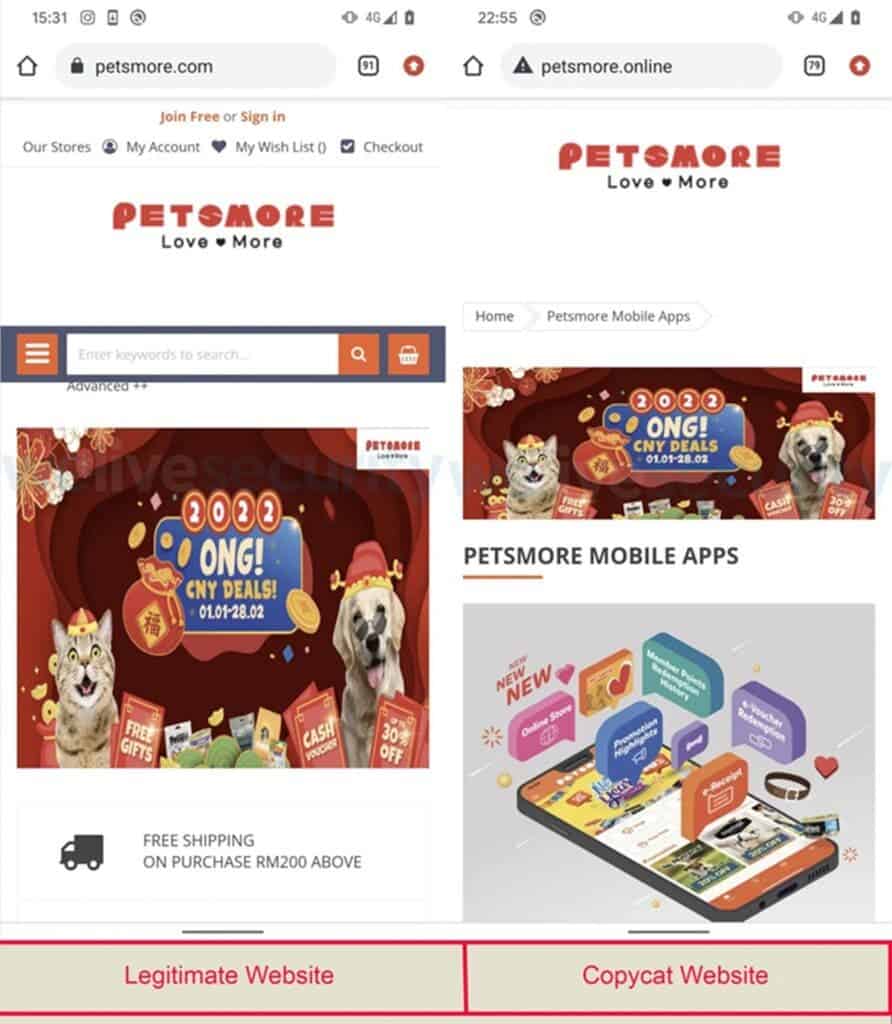
Notably, the copycat websites mimicks MaidACall, Maideasy, YourMaid, Maid4u, Maria’s Cleaning, and Grabmaid. Aside from this, the fake website impersonates a pet store called PetsMore, which is an online pet store for Malaysian users. In its report, the cybersecurity firm revealed that the threat actors attempt to steal banking credentials through these fake e-shop applications. Furthermore, these apps can access and forward all SMS messages with 2FA codes from the bank to the hacker operating the malware.
This comes at a time when Malaysia is facing a major power crisis due to illegal crypto mining in the country. Furthermore, the hackers are targetting customers of the Hong Leong Bank, Bank Islam Malaysia, BSN, and RHB. Aside from this, they are phishing for the banking credentials of CIMB Bank, Public Bank Berhad, Affin Bank, and Maybank customers. Facebook ads are teeming with links to these websites that encourage users to download what appear to be Android apps available on the Google Play Store. However, when the victim clicks on these links, they are directed to malicious servers that the hackers control.
Hackers Aiming To Steal Bank Data Of Users In Malaysia Through Fake Apps
To recall, Google Play Store received a more personalized scoring mechanism for an improved app evaluation system last year. This significant feature allows users to decide whether to download and install an app on their device. However, these hackers particularly target potential victims that have enabled “Install unknown apps” options on the phones or any other device. In fact, this is a prerequisite for this hack to succeed. Moreover, five of the aforesaid services do not have an app on Google Play.
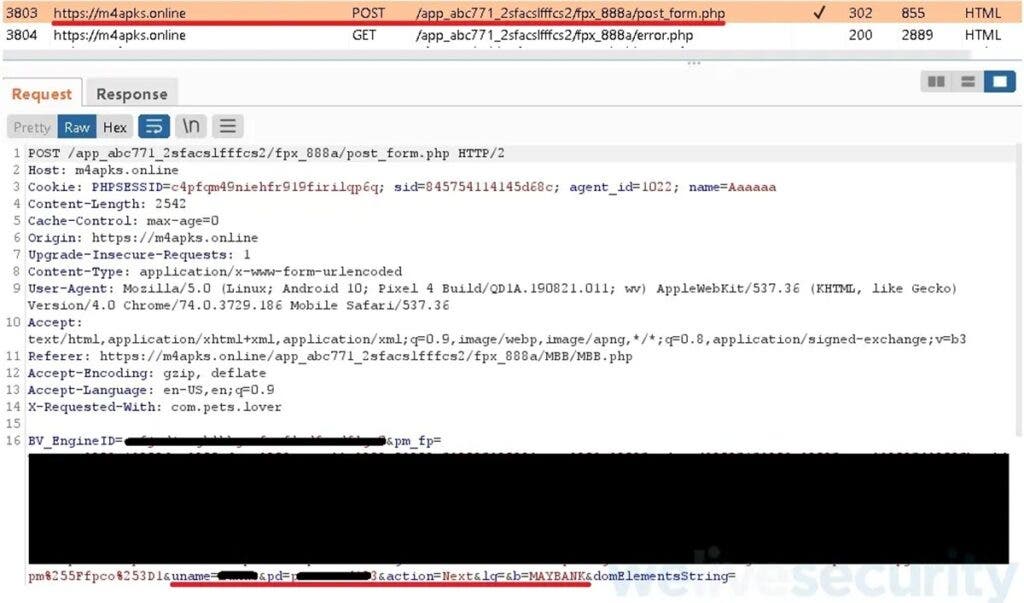
After launching, the apps urge users to sign in to their accounts to place their orders, that are actually fake. Now, users get a prompt to complete the checkout process which includes transferring funds from their bank accounts. Once they pick the direct transfer option, victims get a fake FPX payment page. Here, they can choose their bank from the eight Malaysian banks. Next off, they are prompted to enter their credentials, as per ESET malware researcher Lukáš Štefanko.
The campaign aims at stealing the banking credentials that the victim enters. Moreover, these details then go to the server which the hacker controls. In the meantime, the victim receives an error message that claims the user’s ID or password is invalid. Furthermore, these fake apps can access and forward all SMS messages the victim receives to the attacker-controlled server. So, the hacker can access details even if the victim has two-factor authentication on their accounts. According to Štefanko, the campaign is likely to target other countries and banks in the coming days.