This Android malware spies on your messages to steal your financial data
androidTuesday, 21 June 2022 at 09:02

The first time we told you about it was in 2021. BRATA Android malware had just been discovered by Cleafy researchers, at the same time as it arrived in Europe. Its operation was already chilling: through a phishing campaign, hackers manage to convince their victim to download their malware, which they disguise as a fake anti-spam application. Once installed, the user loses control of their smartphone, giving access to their bank details.
Already particularly dangerous, BRATA did not stop there. At the beginning of 2022, hackers deploy an update capable of reconfiguring the Android smartphone to factory settings, at the same time making the malware completely undetectable. Today, Cleafy researchers have made disturbing new discoveries. Several novelties have indeed slipped into the process, starting with phishing pages which can now spy on the victim's messages.
BRATA malware for Android now has advanced mobile threat capabilities
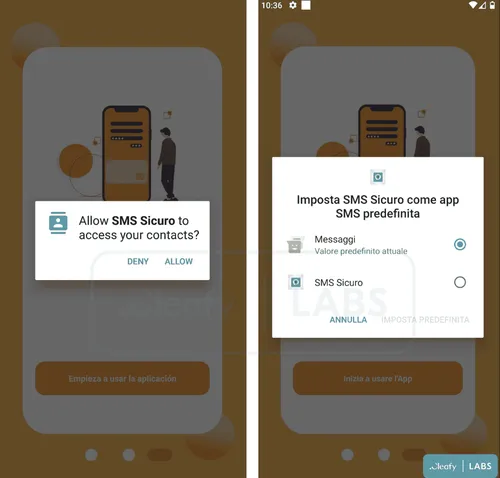
As we highlighted through our metrics, when a new release comes out there are also new features that make it more dangerous. During the last months, a new BRATA.A variant has been spotted in Android smartphones in the EU territory posing as specific bank applications, including some internal changes like a new phishing technique in charge of mimicking a login page of the targeted bank.
This technique has two major advantages. First, it allows BRATA to retrieve the two-factor authentication codes needed to log in to certain accounts. Second, the malware automatically detects all usernames and passwords that are in the victim's conversations; thereby compromising their entire online life.
In addition, BRATA has visibly changed its strategy. As Cleafy explains, the malware “now focuses on targeting a specific bank for a few months; before moving on to another target”. Finally, it installs a backdoor on the victim's smartphone to open the way to potential future attacks of another nature. Now more than ever, be very careful of what you install on your Android phone.
Loading






