Malware-Injected App in Google Play Store Goes Undetected for Over a Year!
GoogleSaturday, 27 May 2023 at 06:29

Both Apple App Store and Google Play Store are known to have multiple security features. All of them keep the users safe from the malicious app and protect their data from getting into the wrong hands. But regardless of all the security features that these open marketplaces come with, there’s always a risk.
For example, a popular app named iRecorder Screen Recorder has been caught doing malicious work. It first appeared on Google Play Store back in 2021. And ever since then, it has been a go-to option for many who wanted to capture screen content. But since 2022, it has been spying on all the users and collecting their data.
iRecorder Screen Recorder Had Malware For Almost A Year Without Google Play Store Noticing It
The previous versions of the app did not include any malware. It was simply a useful tool that allowed you to record the screen. But just over a year after the launch, the app was updated in the Google Play Store. And according to ESET investigation, that update came with malware, which affected millions and millions of users.
Want to know what did the malware in the app do? ESET explains that it secretly recorded audio and forwarded the recorded files to a remote server. The spying tool that the developers used was a code from AhMyth. It is an open-source remote access Trojan (RAT). And iRecroder Screen Recorder is not the first app to come with it.
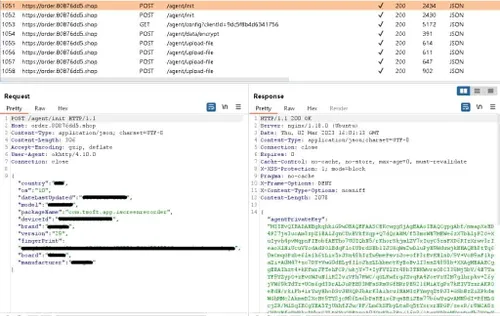
There have been many other apps with the same spying tool. And interestingly, all of these apps were undetected by Google Play Store’s security features. That said, unlike the other malware-injected apps, iRecorder Screen Recorder pulled up a very cunning trick.
That is, it gets the permission that the malware needs to do all of its nasty business directly from the user. After all, the app requires some additional permission to perform screen recording. And as it is categorized as a screen recorder app, neither Google Play Store nor users bothered to take a look into it.
Google's Swift Response
After the issue, Google immediately removed the iRecorder Screen Recorder app from the Play Store. However, if you have installed the app before, you should uninstall it right away. In addition to that, you should clear the app’s files.
Nonetheless, this analysis serves as a prime example of how vulnerable the Google Play Store actually is. Any app can function normally and suddenly turn dark. And when it does, it can stay in shady operation for months without getting caught.
The researchers theorize that these apps do not have good motives to begin with. They function normally to build up a proper user base. And when the number of users is good enough, the developers inject malware into them and start collecting user data. However, the researchers noted that they don’t have any evidence to prove the theory.

ESET also suggests that the app might be a part of an active espionage campaign. That means there could be many other tools in the Google Play Store that seem normal but might hide malware. So, it would be a great time to check what apps are installed on your Android phone at the moment.
That said, it’s true that Google Play Store’s preventive measures regarding these apps are now underscored to be ineffective. But the good news is Google is currently experimenting with new methods to stop these apps. And with Android 14, these experimental features may see a final release.
There’s no guarantee that the new methods will successfully help Google Play Store prevent these malicious apps. But it’s still an important indication that Google has been taking app security seriously.
Loading