The menace of Anatsa malware continues to loom over Android users, demonstrating a resilience akin to infamous threats like Joker. First surfacing in 2021, Anatsa has proven its ability to evolve, eluding detection and devising more intricate variants. The malware’s primary objective remains unchanged: to surreptitiously infiltrate Android devices and abscond with users’ hard-earned money. In a recent analysis conducted by Threat Fabric, the latest campaign of Anatsa reveals a heightened sophistication, allowing it to circumvent Android security measures and manipulate banking applications for financial theft.
Unveiling the Persistent Threat of Anatsa Android Malware: A Closer Look at Its Evolving Tactics
Anatsa’s Ingenious Modus Operandi
Android malware typically operates through two primary methods: exploiting accessibility services and downloading malicious code post-installation. Google has been vigilant in addressing the former. Restricting accessibility services to specific applications and limiting their usage to those installed from trusted sources. However, these measures have proven insufficient in thwarting the ingenuity of malware developers.
Threat Fabric highlights that malicious actors often camouflage their malware within seemingly legitimate applications on Google Play, justifying the use of accessibility services. For instance, a purported system cleaner app may claim to leverage accessibility services for application hibernation. The next step in the nefarious plan involves promoting the app through fake reviews, propelling it into the Top 3 rankings, and reaching a substantial user base—sometimes exceeding 10,000 installations before removal from Google Play.
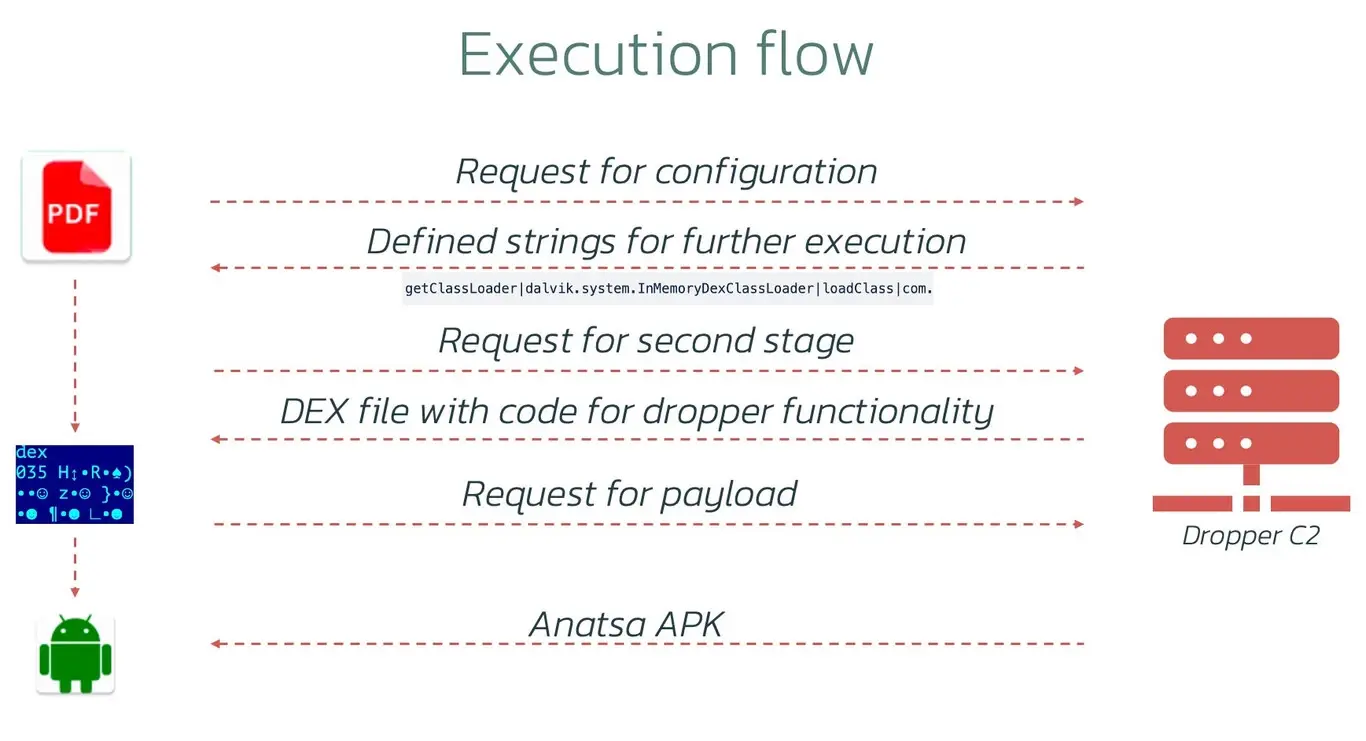
Anatsa employs a dropper technique, wherein the initial application is clean upon installation. However, a week later, it clandestinely downloads the malicious code downloader configuration. This strategic approach allows the malware to evade detection, as the initial application lacks explicit references to remote code download, preventing alarms in detection systems.
The Endgame: Access, Manipulation, and Financial Theft
Anatsa’s ultimate goal is to activate both the malicious code and the accessibility service, enabling it to perform actions without requiring user intervention. This includes accessing sensitive applications like banking apps and executing financial transactions. Threat Fabric underscores the rising trend of seemingly innocuous applications on Google Play transforming into Trojan horses, bypassing the protections introduced in Android 13.
In Android 13, applications from external sources cannot activate the accessibility service until restrictions are lifted. However, Anatsa sidesteps this constraint by infiltrating devices through Google Play, where such restrictions do not apply. As a result, users are advised to exercise caution, avoiding the temptation to trust unknown applications solely based on their high rankings within the application store, especially when seeking accessibility permissions.
Guarding Against the Anatsa Android malware
Protecting oneself against evolving threats like Anatsa requires adherence to conventional security practices. Users are strongly urged not to trust unfamiliar applications, even if they boast top positions in the application store. The heightened risk associated with apps requesting accessibility permissions demands a cautious approach. Malware creators continue to adapt their strategies to exploit Android vulnerabilities. Emphasizing the need for users to remain vigilant and discerning in their app choices.
Conclusion
The saga of Anatsa malware persists, presenting an ongoing challenge for Android users. As the threat landscape evolves, it is crucial for users to stay informed, adopt prudent security measures, and exercise discretion when granting permissions to applications. By understanding the evolving tactics employed by malware like Anatsa, users can fortify their defenses and navigate the digital landscape with greater resilience against financial cyber threats.





