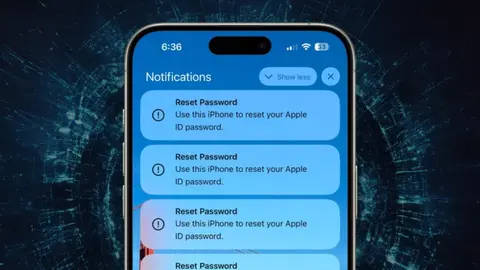
One of the recent threats targeting iPhone users involves malicious parties exploiting the Apple ID password reset system to bombard users with iOS prompts, potentially compromising their accounts. To safeguard against these iPhone password reset attacks, commonly referred to as “MFA bombing,” consider the following precautions.
We recently learned that Apple users are facing a new type of attack called MFA bombing. This attack, also known as MFA fatigue or push bombing, isn’t brand new, but it’s causing trouble. It tricks people by sending them official password reset messages on their iOS devices.
According to a report by Krebs on Security (cited by Parth Patel), attackers are exploiting this vulnerability by targeting an Apple user’s phone number. They bombard iPhones and other Apple devices with over 100 multi-factor authentication (MFA) prompts, urging users to reset their Apple ID password.
Guide to Protect Yourself Against iPhone Password Reset
- Making use of the “Don’t allow” button:
Since the password reset requests come as system-level alerts, they may seem convincing. However, it’s important to select “Don’tAllow” for each of them.Attackers often tire victims by sending them many messages. They might do this for several days in a row. The victims have to keep saying “Don’tAllow” to these messages. You can use step 3 if needed.
If you notice a password reset message while browsing online, it could be a trick by scammers. Close the webpage immediately because both buttons could take you to a harmful link.
- Avoid all calls, even if it looks like a call from Apple support:
Attackers are tricking people with call spoofing. This makes it seem like the call is from the real Apple Support number. They might even ask for personal information to make the scam seem real.After that, they’ll attempt to obtain a one-time passcode from you to gain control of your Apple account. If you’re unsure about a call, it’s best to reject it. Instead, call Apple directly back at 800.275.2273 (for the US). Call spoofing shouldn’t be able to interfere with your outgoing call to the authentic Apple Support.
Apple emphasizes that it won’t make outbound calls unless you ask them to. Also, remember never to share one-time codes with anyone.
- Change your Apple ID phone number:
If you keep receiving the prompts, changing your phone number linked to your Apple ID should make them stop. But remember, this might affect iMessage and FaceTime.
Conclusion
Hopefully, Apple is working on a solution to prevent malicious parties from exploiting this system. However, users have been reporting the password reset scam for at least two years, and possibly even longer.
A recent victim shared that a senior Apple engineer suggested enabling the Recovery Key feature for his Apple ID to stop the password reset notifications. However, further testing revealed that this was not effective. Krebs on Security confirmed that Apple Recovery Key does not prevent reset password prompts.
As stated in Krebs on Security’s article, there seems to be an issue with the rate limit in the Apple ID password reset system. Explaining further, Krebs on security quoted:
What sanely designed authentication system would send dozens of requests for a password change in the span of a few moments, when the first requests haven’t even been acted on by the user? Could this be the result of a bug in Apple’s systems?
Hopefully, Apple will work out a permanent solution soon as these attacks keep getting common. We all know Apple to be a company that prioritizes security of its users over everything else. While the company may be working to fix this issue, it is advisable to take the security tips above seriously and stay safe from such attacks.