Security Alert: NGate Android Malware is Draining Bank Accounts via NFC
PhonesMonday, 26 August 2024 at 03:04

A new serious threat to Android users has surfaced: NGate Android malware. It exploits the NFC chips to steal credit card data. This malicious software can relay the data read by the NFC chip to an attacker's device. This enables them to emulate victims' cards and make unauthorized payments or withdrawals.
The campaign using NGate malware has been active since November 2023. It is connected to a recent report by ESET on the increased use of progressive web apps (PWAs) and advanced WebAPKs to steal banking credentials from users in the Czechia.
In addition to stealing credit card data, the NGate malware can perform direct cash theft. So this isn't like some of the other malware that have surfaced before.
How Does NGate Android Malware Steal Card Data via NFC Chip
The attacks begin with malicious texts, automated calls, or malvertising. These trick victims into installing a malicious PWA or WebAPK. The apps may seem like urgent security updates, but they steal client access credentials.
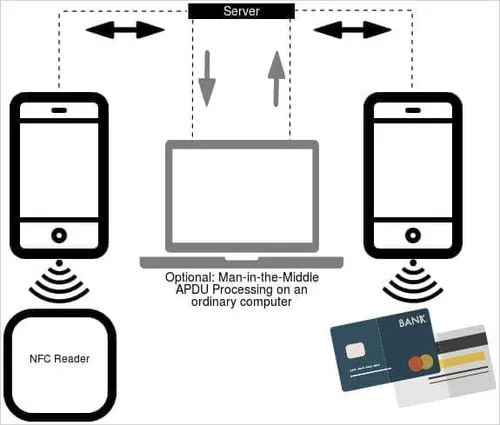
Image source: ESET
These apps do not require permissions and abuse the browser's API to access the device's hardware. After the phishing step, victims are tricked into installing NGate.
NGate uses NFCGate, an open-source tool for NFC testing, to capture NFC data from payment cards. The attacker can save this data as a virtual card and replay it on ATMs or PoS systems.
ESET's malware researcher, Lukas Stefanko, demonstrated how NGate can capture card data in wallets and backpacks. An attacker could use this data to make contactless payments or clone NFC access cards.
How Does the Malware Acquire Card Pin
To withdraw cash from ATMs, the card's PIN code is required. The researchers found that scammers obtain this information through social engineering.
After the PWA/WebAPK phishing step, scammers call the victim, pretending to be bank employees. They inform the victim of a security incident and send an SMS with a link to download NGate.
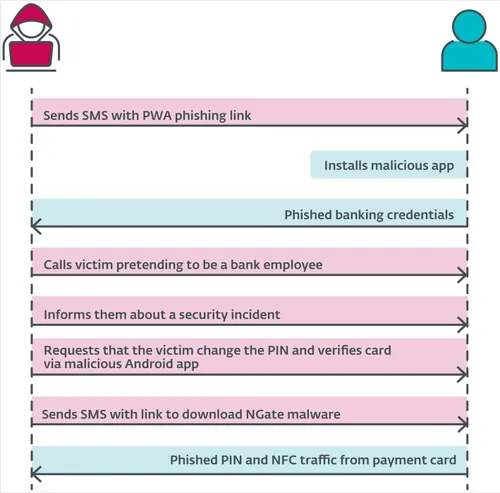
Image source: ESET
The victim scans their card and enters their PIN to "verify" it on the malware's phishing interface. This sensitive information is then relayed to the attacker.
Czech police have already caught one cybercriminal performing these withdrawals. However, this tactic poses a significant risk for Android users.
ESET also warns that cloning access tags, transport tickets, and ID badges is possible.
To mitigate the risk, you can disable your device's NFC chip. If you need NFC activated, scrutinize app permissions, install bank apps from official sources, and be cautious of WebAPKs. WebAPKs are small, installed from browsers, and do not appear under '/data/app' like standard Android apps.
Popular News
Latest News
Loading

