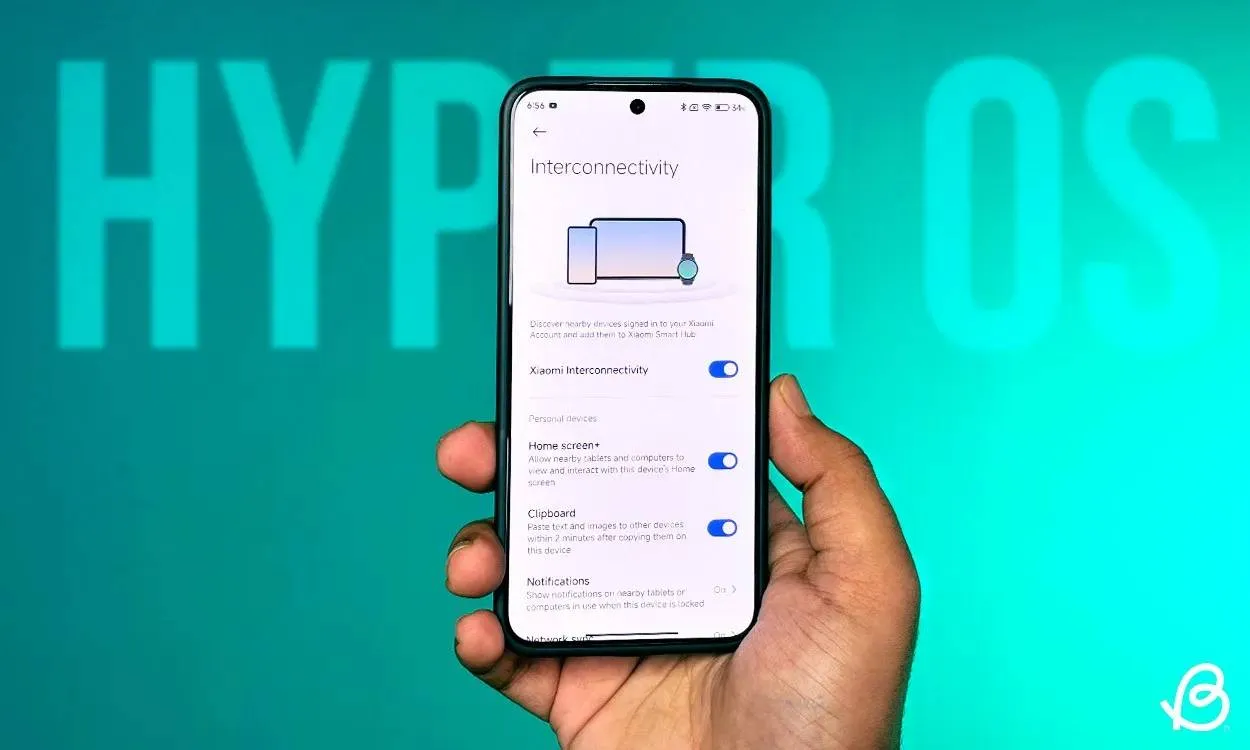
OnePlus 16 Tests 200MP Sensor with LUMO Image Processing
Mar 07, 17:38
OnePlus 15T Leaks Reveal Compact Design and Premium Features
Mar 10, 10:30
I Flew the World’s First 360 Drone, and Now Everything Else Feels Limited
Mar 09, 13:35
Vivo X300s Targets Gamers with 144FPS MOBA Support and War Drum Speakers!
Mar 09, 09:52
Xiaomi 18 Poised to Redefine Interaction with Advanced AI Features
Mar 07, 14:24
OnePlus 15T Leaks Reveal Compact Design and Premium Features
OnePlus 15T compact phone leaked: 6.32-inch screen, 71.82mm narrow body, 194g weight. Hands-on demos start March 12 at offline stores.

Xiaomi Tests Modified 17 Ultra with Magnetic Component System?
Modified Xiaomi 17 Ultra variant leaked with 6.6-inch modular magnetic design. Smart Pikachu reveals experimental thin and light model.

Midea Launches Self-Evolving Smart Home System at Shanghai Conference!
Midea MevoX self-evolving smart home launched March 10 in Shanghai. Continuous memory learns habits for intent-driven automation.

Vivo V70 FE Goes Official With 200MP Camera and Massive Battery
Vivo V70 FE launches with a 200MP camera, 7,000mAh battery, Dimensity 7360-Turbo chip, and 120Hz AMOLED display. Starts at $380.
- Great insights on the Honor Watch GS 5 features! The 23-day battery life and advanced health tracking tools make it a strong competitor in the wearable market. At Hezire Technologies, we’re also seeing growing interest in smart wearables that offer long battery performance and accurate health data feedback. Users in Dubai and the UAE are always asking for reliable devices that support active lifestyles — and watches like the GS 5 really fit that need. Thanks for the detailed specs!
 heziretechnologies19-02-2026
heziretechnologies19-02-2026 - I want to know how much the Oppo Pad 4 Pro tablet is currently priced please?Egyptian13-02-2026
- I want to know how much is the price of the Oppo Pad 4 Pro tablet currentlyEgyptian13-02-2026
- We hope that the giant Xiaomi will put a cooling fan in the global version of the Xiaomi 17T Pro phone as in the Redmi K90 Ultra, albeit with less capabilities, and that the battery will be larger than 7500 mAh, and the screen will reach 6.85 inches.Egyptian12-02-2026
- Most of the tablets doesn't support Zoom video blur background feature.YugeshM1509-02-2026
- 👍️CajunMoses03-02-2026
- Besoin de ça
 merveil11-12-2025
merveil11-12-2025 - Looking forward to buying both sizes of this when they are available in Thailand 🇹🇭chrisman08-12-2025
- Finally! Surprised corrupt Grok was not mentionedMaxNix07-12-2025
- About time!!MaxNix07-12-2025

Mark Gurman Reveals iPhone Ultra Foldable Priced Above $2,000
Apple's foldable iPhone dubbed "iPhone Ultra" costs over $2,000 with large display and under-display sensors. Mark Gurman leak details.

Wide-Screen Foldables and Super-Large Air Models Launch Q4 2026
Wide-screen foldables and super-large Air models launch 2026. Continuous price increases expected throughout year. Q4 phone trends detailed.

Xiaomi Book Air leaks with ~1kg weight, Panther Lake processors, and up to 32GB RAM!
Xiaomi Book Air leaked with ~1kg weight, Panther Lake processors, and up to 32GB RAM. Premium ultra-light laptop targets flagship market segment.
Top 6 WhatsApp settings to turn on to keep your account safe and how to activate them
WhatsApp is where most of our daily talks happen. Chats with friends, work updates, photos, and even bank alerts all go through it.
Loading